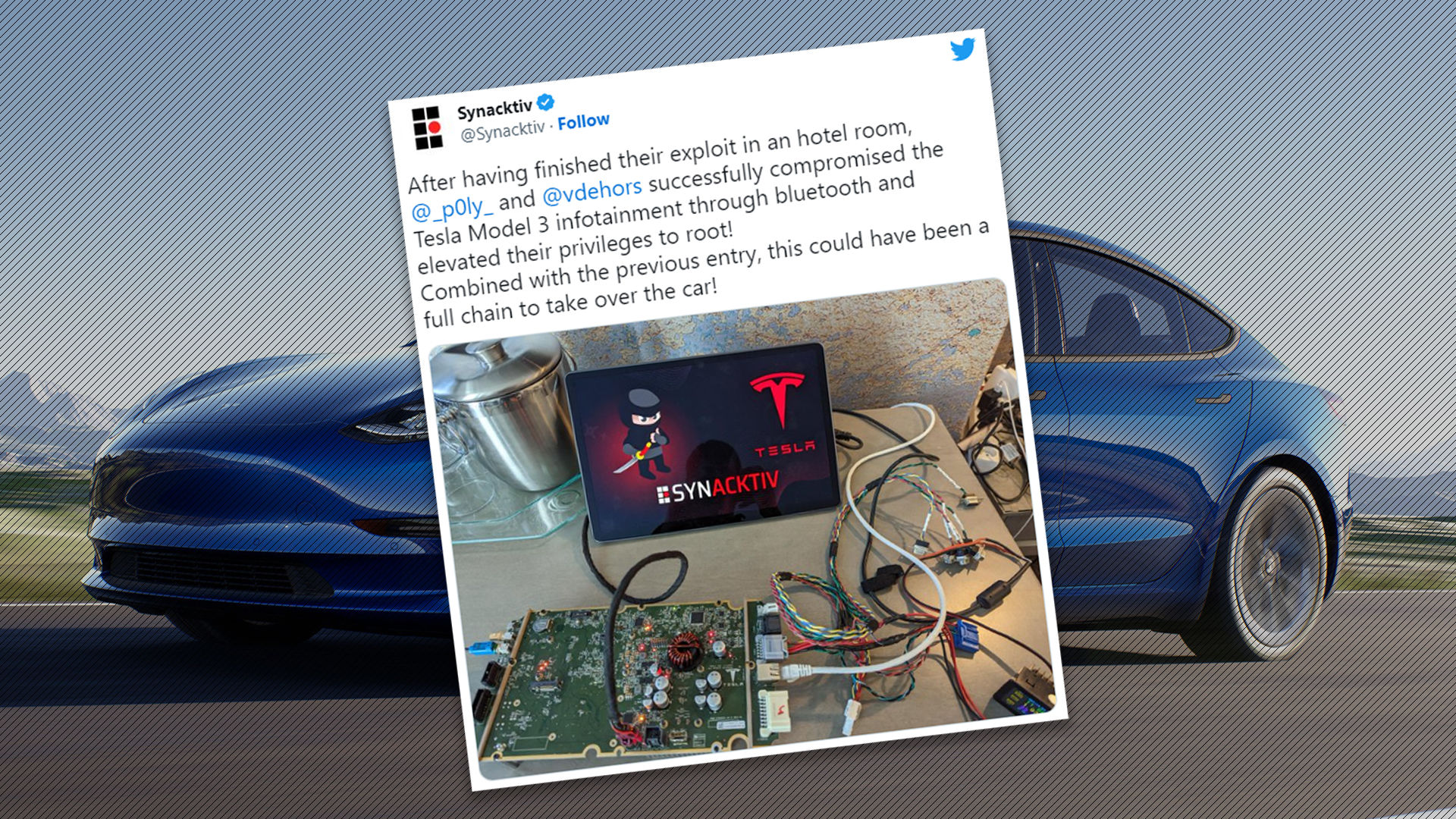

A team of ethical hackers competing in the Pwn2Own 2023 hacking conference held in Vancouver last week won a Tesla Model 3 and $350,000 after successfully exploiting the infotainment system of the car.
The security researchers, which collectively go by the team name Synacktiv, were given 10 minutes to hack the isolated infotainment system of the Tesla. The screen was set up on a bench and within four minutes of the countdown starting, the team was able able to gain full access to the car’s critical systems, effectively compromising the vehicle fully.
Now, you may notice that this hack wasn’t actually performed inside the car. The infotainment screen was removed from the vehicle to isolate the environment and prevent any unexpected behaviors with the vehicle itself. Still, the screen was plucked directly from the Tesla and ran the vehicle’s operating system just as if it were in the car.
“Of course, we would like to do this on a car itself but there are just too many variables that would make it potentially dangerous for those around the vehicle, including the building vehicles parked by, so we do not want to take that chance,” said Dustin Childs, head of threat awareness at the Zero Day Initiative. “We prefer a nice controlled environment.”
Within two minutes, the team had successfully executed the first part of their attack chain against the Tesla, rebooting the infotainment screen and displaying their own logo.
While the technical details of the exploit are still under wraps, it was made public that Synacktiv’s attack chain made use of a time-of-check to time-of-use (TOCTOU) attack, which is effectively an attack that “races” to exploit the system’s desired actions. For example, the Tesla’s system may check to see if a specific file exists, and within the time it takes to check if the file exists and launch it, the file was replaced with one that permits the exploit to be launched.

According to the Zero Day Initiative, the attack was so sophisticated that it actually earned Synacktive the first-ever “Tier 2” award. This meant that along with its initial $100,000 in winnings for the attack, the team also banked a $250,000 bonus plus various other smaller payouts.
The total combined prize value handed out at Pwn2Own was $1,035,000, and Synacktiv came out with more than half—a whopping $530,000, plus the Model 3 that it won. Last year, the team also earned $75,000 by demonstrating a zero-click exploit against a Tesla.
While it seems scary that hackers are out there actively finding holes in the security of connected vehicles, it’s actually beneficial. By giving incentives to security researchers, automakers are essentially out-bidding bad actors who develop these kinds of attacks for nefarious purposes or other entities who might purchase the exploits for their own gain.
It’s worth noting that some automakers don’t offer such bug bounty programs, let alone any sort of formal way to report security flaws with their products. Tesla offers a bug bounty program that awards researchers up to $15,000 per finding.
Got a tip or question for the author? Contact them directly: rob@thedrive.com